TRACING E-MAIL
TRACING E-MAIL
Hello friends today in my article I'll tell you how can you you trace your e-Mail's on Internet but before starting i Just want to ask something from you....
- Are you receiving abusive e-mails from unknown people?
- Are you being blackmailed or threatened through e-mail?
- Are your children receiving e-mails filled with adult contents?
All e-mails communications on the Internet is governed by rules or regulation, which is sub divided into two different protocols:
- SMTP (SIMPLE MAIL TRANSFER PROTOCOL) (Port 25)
- POP (POST OFFICE PROTOCOL) (Port 110)
Generally, the path taken by an email while traveling from sender to receiver can be explained by following diagram.
E-MAIL HEADERS
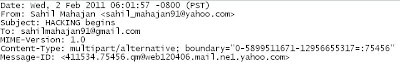
The most effective & easier way to trace an e-mail is to analyze its headers. Most cyber crime investigators turn to e-mail headers for evidence in any kind of e-mail related crime. E-MAIL headers are automatically generated and embedded into an e-mail message both during composition & transfer between system. A typical e-mail header looks something like this:
To read the e-mail header you have to start reading it from bottom, there are several puzzle pieces which you have to solve. In example or for simple understanding divide the e-mail header into 2 part:
This part of header tell you the e-mail sent from Sahil Mahajan <sahil_mahajan91@yahoo.com> to sahilmahajan91@gmail.com with Subject: HACKING begins on Date: Wed, 2 Feb 2011 06:01:57, MESSAGE ID is very useful part of e-mail, many crime investigation companies use this ID code to solve cases.
In another part of the email header is very critical portion of the e-mail, which contains the sensitive information about the path traveled by e-mail. bottom to up rule is implemented to read this part of e-mail.
Received: from [218.248.64.165] by web120406.mail.ne1.yahoo.com via HTTP; Wed, 02 Feb 2011 06:01:57
This is the last received line in the email header their we examine in above picture, it shows that someone using the IP [218.248.64.165], this is the source system from which the e-mail is delivered to mail server, trace this IP address and you can easily find the Sender from which you receives the fake or abusive e-mails. Tracing e-mails have many faces but due to some security reason we cant reveal them but by simply following this method you can easily detect any unknown sender who send you fake mails....
Hope this is informative and if u have any question, query or any suggestion kindly post us.






I'm having some kinda strange feelings about my partner, I hired HACKERLITE50@gmail.com and they got me full access to her phone in few hours.
ReplyDelete