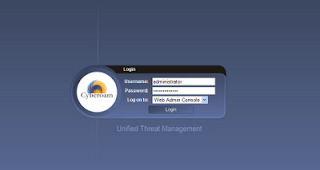
HOW TO FIND HIDDEN PASSWORD UNDER ASTERISKS

Welcome to "BLACKBACKHAKERS - An approach to introduce people with the truth of HACKING". Often we use the " Remember Me " feature in most form logins to help the signing in process faster. But taking advantage of that sometimes makes us forget what our real passwords are. If you often stare at the asterisks and wonder what’s your actual password, try this trick. Thais trick only work for Mozilla Firefox. Add on : Show My Password To reveal password under asterisks just double click on text box where password is saved.