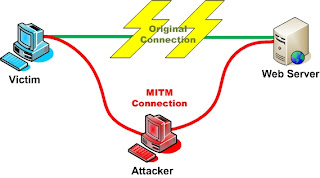
Packet Sniffer for Android phones

This is a nice app to capture and display WiFi and bluetooth traffic on Android phones. But for using this app, you have to root your phone and have "su" command install. This app is based on the tcpdump package therefor it have to be installed manually. 1. Download and Install PacketSniffer App from the market or from the following link. 2. Copy the precompiled TCPDUMP file to the "/data" library on your phone: first make sure your "/data" library has READ and WRITE privileges. if not use: "chmod 777 data" in order to copy use the following command if you have ADB :"adb push c:\locationOfTheTcpdumpFile /data" in case you don't have ADB you can copy the tcpdump file to the SD card and do: "cat /sdcard/tcpdump > /data/tcpdump 3. Give the tcpdump file Read Write and Exec privileges : ...