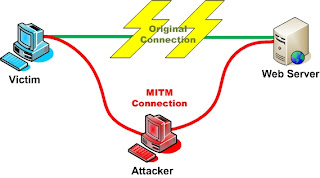
MAC Address Spoofing

MAC Address Media Access Control (MAC) address is a unique identifier or a serial number assigned to a network interface. This unique identifier is used in the Media Access Control protocol. It is hard coded in the read only memory of your NIC (network interface card). MAC addresses are used for routing packets between physical devices (i.e. network interface cards) on networks. Most important thing is that no two NIC card in the world can have same MAC address. MAC Spoofing MAC Spoofing is the way of changing the MAC address of a NIC on a network. By using MAC Spoofing, you will never by pass server access control list. It is only used to hide your identity on the network and it allows network devices to impersonate another network device. In IP Spoofing, response came to the original MAC Address Spoofing With SMAC SMAC is a nice tool that can help you in spoofing MAC address of your NIC. This tool is available for Windows and works on Windows VISTA, XP, 2003, and 2000 sy...